# Android AppSealing
Android AppSealing provides a wide range of security measures. Among them, we have patented technology that allows us to protect your apps's memory and code from being hacked and stolen. The sealing will add the security module to your app. Then, the security module in the sealed app will launch along with the game to protect it.
For Android AppSealing (console) :
- Open the ADC console at https://console.appsealing.com (opens new window)
- Login with appsealing account credentials
- In the navigation pane, choose 'Android AppSealing'
Contents

# Apply AppSealing
AppSealing provides self-protection features like code protection, integrity protection, rooting detection, cheat tool and emulator detection without ANY CODING.
Things you should aware before starting with AppSealing
- Platform - App Platform on which application is built, which can be iOS or Android
- Framework - Framework use to build app, In case of hybrid frameworks like react you should know which react version was used for development
- KeyStore Info - Once app is sealed and ready to release in playstore, you can either sign sealed app by yourself or can use AppSealing to sign it which requires keystore information
# Sealing App
Applying AppSealing mobile app security takes only 3 steps
- Configure sealing options at ADC or using CLI tool. Based on features sealing options are divided into multiple sections like mandate fields, general features and advanced features
- Upload your app and apply AppSealing. You can either upload android app as apk file or aab file. AppSealing also provide feature to secure JS files for React Framework where you can upload zip files.
- Download signed app with keystore configuration or un-signed app via apksigner
Sealing options provide customization to security applicable while sealing app, they are segregated as below:
- Mandatory fields consist of set of fields related to application like app framework, category, framework version etc. Details are mentioned in metrics mandatory fields section.
- General Features contains security options that can be enabled or disabled based on your requirement. To ensure complete security block all the features to restrict vulnerabilities, more details for options are provided in metrics general features.
- AppSealing provides advanced set of functionalities that can protect not only application but also data used by App like Data Sealing or Custom Blacklist. Navigate to advanced features for more information.
Based on the sealing options user can view the security level on right top section. This gets updated based on the AppSealing Version and Sealing options. Once the sealing options are configured user can upload application by drag-drop or selecting upload button and click on "Apply AppSealing" to start sealing. Sealing will start securing your application and will prompt download using window, you can also download sealed apps later from Historical Information.
# Metrics
# Mandatory Fields:
| Description | Options |
|---|---|
| App framework | Application framework is platform used to develop your android application. AppSealing supports native as well as hybrid frameworks. Select the appropriate option for your app by choosing option from drop-down |
| AppSealing Version | Details related to sealing versions to be applied on application, use the latest version to access latest security features along with newer framework versions |
| App Category | Game App Security (default) - AppSealing can secure apps built-in unity, unreal and other engines Non Game App Security - For non-game security, Emulator Blocking and Dex Encryption options are automatically applied |
| Sealing Mode | Test (default) - Test mode provides the same level of security, however a periodic 'Test mode' message is displayed on application Release - Release mode removes periodic message of 'Test mode', along with additional features like real time streaming, signing APK's, etc. |
# General Features:
| Description | Options |
|---|---|
| Dex Encryption : Protects JAVA code from tampering by encrypting multiple Dex files. Activating this option may slightly increases app's initial (after install or update) loading time | Yes (default) - Encrypt all classes.dex file to protect Java & Kotlin source code analysis and leakage (recommended) No - It does not encrypt dex files (classes.dex) without encryption, source code is easily exposed, analyzed, tampered and it can be leaked Selective - It can be considered when performance degradation is severe after encrypting the entire Dex files. You can select specific classes and packages that must be protected in your dex files |
| Rooting : Determine whether your app can run on rooted smartphones | Blocked (default) - It detects the rooted device and closes the sealed app (recommended) Allow - The sealed app runs on the rooted device. 'Allow' option makes it easier for hackers to attack |
| Emulators : Set whether your app can run on Android emulators. If you choose to allow emulators, note that until further notice, AppSealing only guarantees protection for BlueStacks and Nox | Blocked (default) - It detects the emulator environment and closes the sealed app (recommended) Allow - Apps can run in an emulator environment Optional - You can select specific emulators to allow, and other emulators are not allowed as a default |
| Work Profile & Samsung Security Folder : In the work profile environment, AppSealing's security features can be disabled. Also, we found some cheating tools are using work profiles to attack devices and apps | Blocked (default) - If a sealed app is launched in the work profile, AppSealing detects it and closes the sealed app (recommended) Allow - The sealed app runs in the 'Work Profile' environmen Optional - You can select specific work profiles to allow, and other are not allowed as a default |
| Macro Tools : Macro tools can be used for purposes other than abusing app. Blacklists are always up to date to block macro tools | Blocked (default) - If a macro tool is detected, the sealed app closes (recommended) Allow - It allows the sealed app running on the device installed with macro tools |
| Packet Attacks : Packet attack tools collect data transferred through the network | Blocked (default) - It detects packet attack tools installed on the device and blocks data leakage and tampering. If a packet attack tool is detected, the sealed app closes (recommended) Allow - The sealed app runs even if the packet attack tool is installed on the device |
| Keylogger : A keylogger is a monitoring tool which hides on the device and collects user's touch information | Blocked - Stop your app when AppSealing detects any keylogger installed (recommended) Allow (default) - Allow your app execution when AppSealing detects any keylogger installed |
| Mirroring app : A mirroring app is a utility tool which can share device's screen to other devices | Blocked - Stop your app when AppSealing detects any mirroring app installed (recommended) Allow (default) - Allow your app execution when AppSealing detects any mirroring app installed |
| Remote access app : A remote access app is a utility tool which allow other device to access the device and can control it remotely | Blocked - Stop your app when AppSealing detects any remote acceess app installed (recommended) Allow (default) - Allow your app execution when AppSealing detects any remote acceess app installed |
| Launch by External App : You can block app launch when hacker execute your app from hacking tool to analyze and attack your app. If your app requires launcher app, then please select 'Allow' | Blocked - Block your app launched by other app (recommended) Allow (default) - Allow your app launched by other app |
Advanced Features:
| Description | Options |
|---|---|
| Data Sealing : DataSealing provides a function that securely encrypts and stores binary file data without additional coding, and allows you to directly read and use the encrypted data, currently supported only for Android Native C/C++ (NDK) | Yes (default) - It detects the rooted device and closes the sealed app No - The sealed app runs on the rooted device. 'Allow' option makes it easier for hackers to attack, If not using turn off 'Data Sealing' service at 'App Configuration' tab to avoid incurring additional costs |
| Custom Blacklist : The custom blacklist is the first feature of Android AppSealing's Over-the-Air update service. App administrators can block suspicious apps that are not blocked by AppSealing's default blacklist | Yes - Custom blacklist you set is updated Over-the-Air with default blacklist of AppSealing No (default) - Disable Custom Blacklist for over the air updates, If not using turn off 'Custom Blacklist' service at 'App Configuration' tab to avoid incurring additional costs |
# Security Guide
- Before AppSealing
Firebase Crashlytics should maintain their original package name without obfuscate to be supported by AppSealing.
Below class must not be obfuscated to check React Native version com/facebook/react/modules/systeminfo/ReactNativeVersion.java.
- After AppSealing
APK
Certificates in the apk is disabled, so you must re-sign your apk with apksigner to install it on your devicesAppBundle (.aab)
To upload your appbundle on PlayStore, appbundle should be signed by jarsigner.
1.1.0.0 version can support React Native version as below:- JavaScriptCore: 0.60+
- Hermes engine: 0.61+
- JavaScriptCore: 0.60+
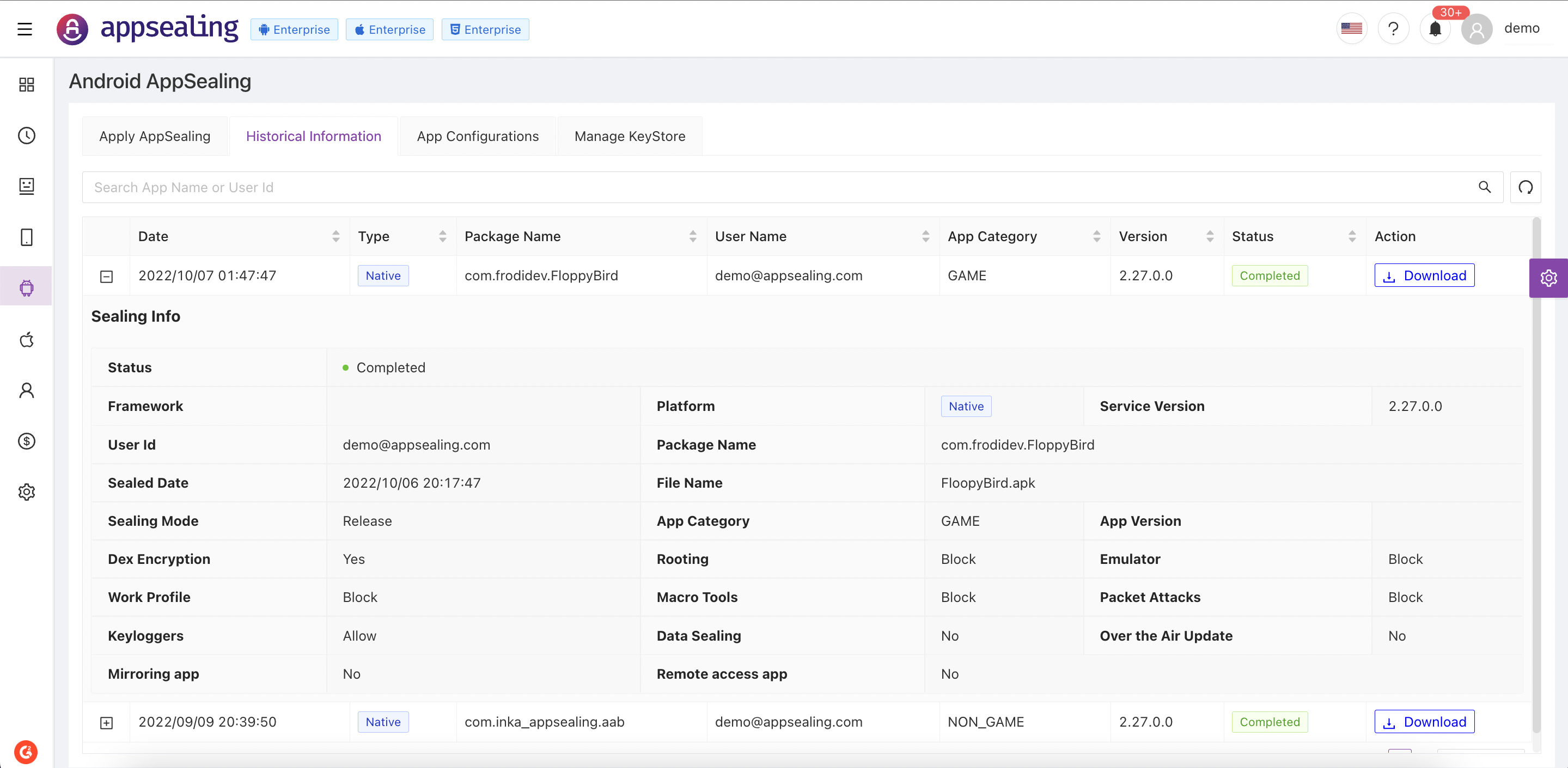
# Historical Information
Historical information tab contains sealing history details for past 30 days. Using this information user can view own as well as team members sealed app configurations. Depending on the status of sealing user can download successful sealed apps or view errors from unsuccessful apps.
Table data is auto fetched at interval of 1mins, but user can also reload data using refresh icon. You can drill down the result set by specifying filters using search bar. This result set contains useful information such as following:
- Time on which threats are reported
- Type of application (Native / Hybrid)
- Android package name
- User Name who sealed application
- App Category (Game / Non-Game)
- AppSealing version
- AppSealing Status(In-Progress / Completed / Failed)
- Action
- Download where user can download successfully sealed app (more details)
- View Errors where user can see errors caused while sealing app
Each record will provide all configurations set while sealing app. To view this details select record and click on '+' icon in first column
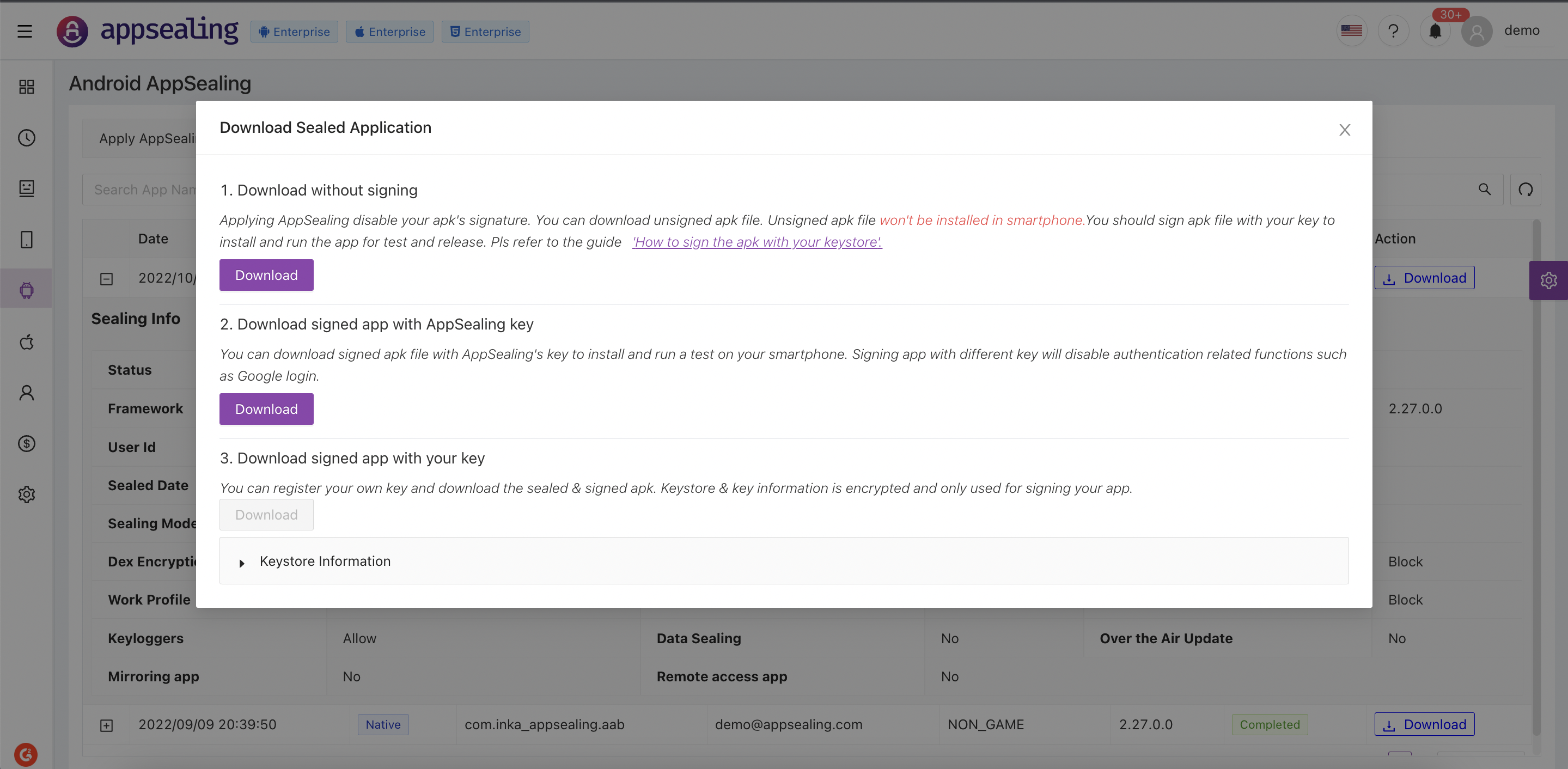
# Downloading Sealed Application
When android app is sealed successfully you will get prompt message to download it. This action is exactly similar to download sealed app from historical information. Sealed app can be downloaded in following ways:
- Download without signing
Applying AppSealing disable your apk's signature. You can download unsigned apk file. Unsigned apk file won't be installed in smartphone.You should sign apk file with your key to install and run the app for test and release
- Download signed app with AppSealing key
You can download signed apk file with AppSealing's key to install and run a test on your smartphone. Signing app with different key will disable authentication related functions such as Google login
- Download signed app with your key
You can register your own key and download the sealed & signed apk. Keystore & key information is encrypted and only used for signing your app
# App Configurations
App Configurations helps to manage your application services. For android apps you can toggle services, manage dex-list, toggle advanced features like data sealing and custom blacklist, etc.
App Configurations displays list of sealed applications by user or team members in card layout. On initial load it will displays 20 apps and further apps can be fetched by clicking "more details" button. Use search bar on top section to filter the apps based on app or package name. Following configurations are available for each application to users:
- Service
If enabled appsealing will track all hacking information for application. This will incur the charges on usage basis, so if not using app or want to stop using AppSealing do turn off the service for respective app here
- Data Sealing
Data Sealing is used to secure your application Data files. It is currently available for Professional users with additional cost and free of cost for Enterprise users. If not using turn off 'Data Sealing' service to avoid incurring additional costs. See how to apply data sealing for more details
- Custom Blacklist
The Custom Blacklist is the first feature of Android AppSealing's Over-the-Air update service. App administrators can block suspicious apps that are not blocked by AppSealing's default blacklist. Currently, the OTA update service is not available in Trial or Professional Plans and can be activated through separate consultations and Enterprise contracts. If you contact the AppSealing business team or the help center, we will provide you with more details. In order to use the custom blacklist, the OTA update service must be activated first. See how to apply custom blacklist for more details
- Manage Selection
Using Manage selection user can update the selective dex. Selective Dex encryption is a feature that encrypts and protects specific dex files built with Java/Kotlin code on Android apps to mitigate any degradation in performance on some apps when all dex files are encrypted. When the app is installed on the device, the dex file is optimized for the device by its system, but the system cannot optimize the dex file encrypted by applying app sealing. See how to apply manage selection for more details
- Transfer Account
You can transfer you sealed application to any account associated with AppSealing. This feature is useful when you using test account for POC's, transfer apps to team members within your organization, etc. See how to transfer account for more details
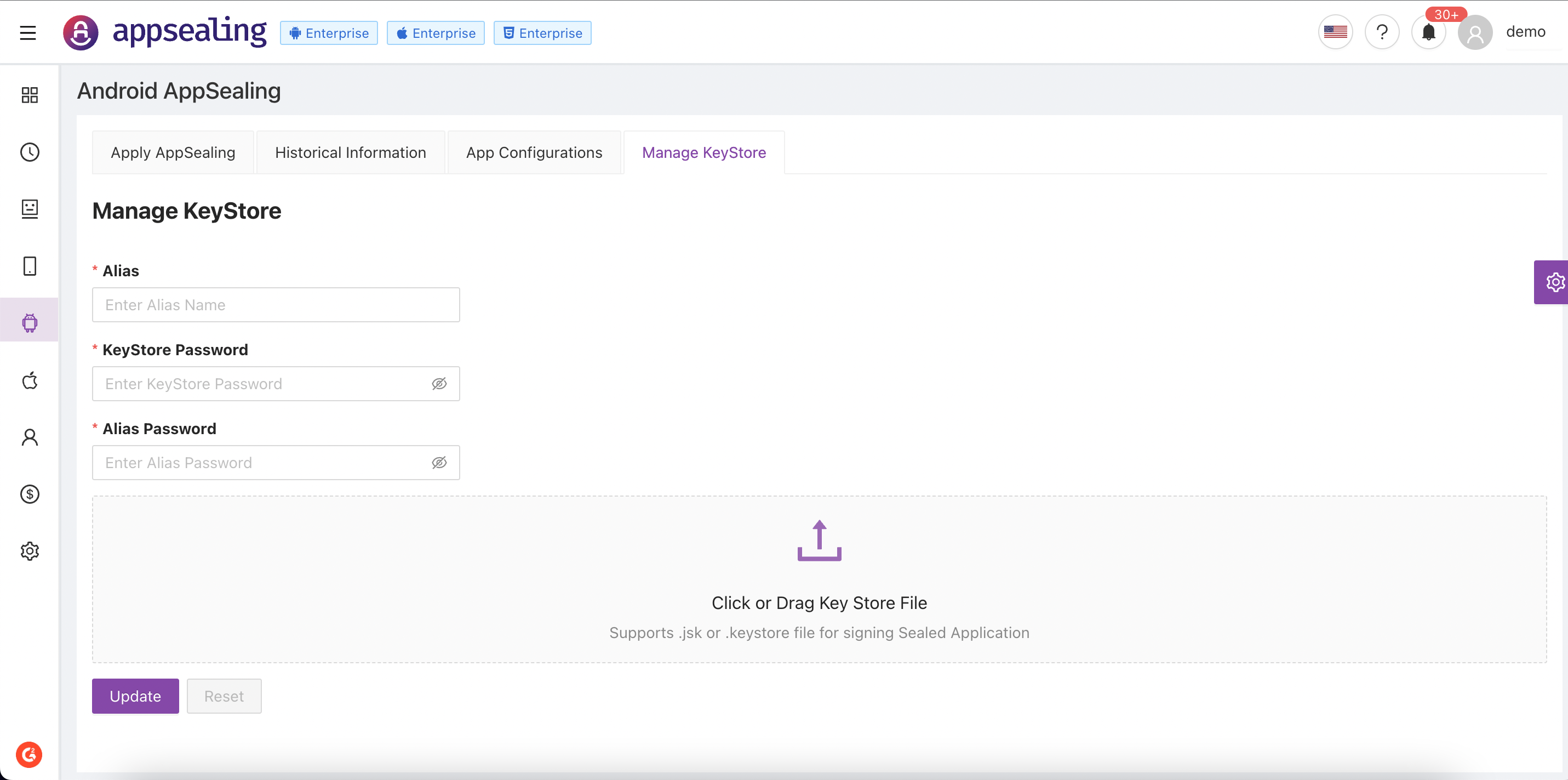
# Manage KeyStore
App developed in android or sealed app cannot be installed on mobile devices unless it is signed with keystore information. Previously user needs to download sealed apk and then sign it manually. ADC provides functionality to download signed apk which can directly installed on devices for testing or launch to external users as well. To achieve this user can maintain keystore information in Manage KeyStore tab.
To register keystore following things are required:
- Alias
- KeyStore Password
- Alias Password
- KeyStore File
Fill all the above information and click on update to save the info. Once it is saved user can download sealed apk and choose "Download signed app with your key" option to download pre-signed app with saved key. You can also delete the keys if not required later as well.